Contents
- Electrum's 2nd DoS attack- What happened?
- Electrum's 1st DoS attack - December 2018
- What is Electrum Bitcoin Wallet?
- How the Electrum DoS Botnet attack works
- How to protect your Electrum funds
- Who's behind the Electrum DoS Attacks?
- Are Desktop and Mobile Bitcoin Wallets Safe?
- Is a hardware wallet safer than desktop and mobile wallets?
It's grown bigger than the Battle of Winterfell.
The latest report on the Electrum Bitcoin Wallet phishing scam on 8 April claims that the DoS botnet attack is far from done and actually getting worse. This follows last week's Ledger Live malware phishing attack and a report on how powerful NSA-created malware is targeting Asian companies.

According to the MalwareBytes report on 29 April, over 152,000 Electrum Bitcoin wallets and computers are currently infected with phishing malware Trojan.BeamWinHTTP and Electrum Stealer, most of them in the Asia Pacific region and Brazil.
This represents an increase of over 10,000 new machines since the massive DoS attack in early April 2019. Over $4.5 million in Bitcoin has allegedly been stolen since the botnet formed less than a month ago.
Electrum's 2nd DoS attack- What happened?
The DoS attack on 8 April 2019 was the second in 4 months on the popular Bitcoin (BTC) wallet for desktop and mobile users. The criminals again used a Denial-of-Service (DOS) attack to block user access to the Electrum servers, then duped them into updating their software on a malicious server from where their funds were stolen. Electrum warned that older version wallets are still at risk and that users must upgrade their software.
Electrum's 1st DoS attack - December 2018
Electrum's latest Denial-of-Service attack was allegedly carried out by a powerful botnet (a large number of Internet-connected devices) which overloaded the Electrum servers and follows a nearly identical phishing incident in December 2018 where 200 BTC were stolen.
Phishing is a scam where a malicious party tricks users into revealing valuable sensitive information such as passwords and bank card details. Examples are SIM swaps, spyware and spam emails.
What is Electrum Bitcoin Wallet?

Electrum is a pioneering open-source Bitcoin software wallet which first launched in November 2011. This lightweight wallet for Bitcoin doesn't require users to run a full blockchain node and is very popular with many crypto owners. Electrum can be installed on both desktop and mobile devices. Here's an in-depth review of this BTC wallet.
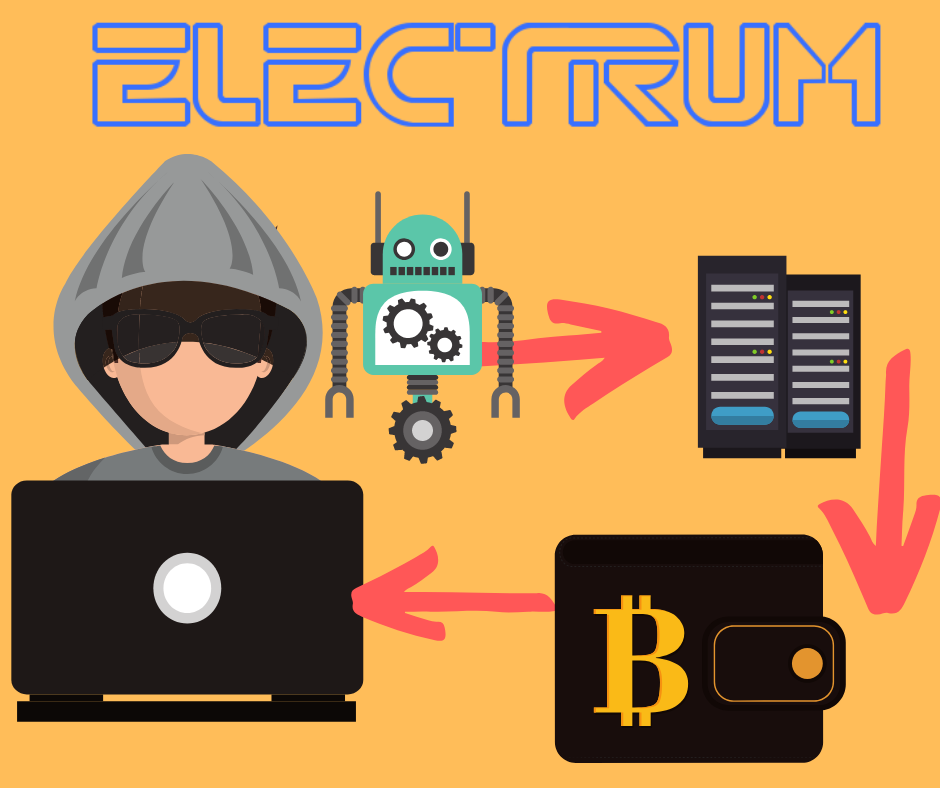
How the Electrum DoS Botnet attack works
- Step 1: Build a Botnet: The hacker(s) creates a botnet, which is a network of compromised personal computers which is infected with bad software and controlled as a group without the owners' awareness.
- Step 2: Leave the Backdoor open: The hackers create a "backdoored" version of the Electrum client, which it then hosts on their own compromised Electrum servers. ("Backdooring" software or an app is basically hacking and modifying an officially released version in order to make it operate differently than intended. )
- Step 3: Flood the server: The botnet targets an Electrum server, making it unavailable to users. It does this by temporarily flooding the server with so many requests that legitimate requests cannot be fulfilled. This is called a DoS attack.
- Step 4: Redirect users: Unsuspecting users who try to access the official Electrum are directed towards a malicious server hosted or controlled by the hackers.
- Step 5: Upgrade to Hacked Version: Users are instructed to sync their compromised Electrum wallet with a malicious server, which then tricks them to upgrade their old software with a hacked copy.
- Step 6: Bye Bye Bitcoin: Once upgraded, hackers have access to the user's funds the next time to log in with their private key. As soon as that's done, all user funds on the old wallets there for the taking by the malicious party.

DoS attack vs DDoS attack
Most of you have probably also heard of a DDoS attack. A DoS attack differs from a distributed-denial-of-service (DDoS) attack, where the incoming traffic attack comes from many different sources, often thousands of IP addresses, too many to block simultaneously.
Both DoS and DDoS are very sophisticated and serious security attacks that can cripple any online entity, even if it doesn't succeed.

Example: Imagine a massive protest or riot outside a building, where a crowd of people blocks the door and effectively stops real customers from going inside, leading them to try and find different ways to access the building.
Why did the Electrum attack happen?
According to lead Electrum developer Thomas Voegtlin, the hacker(s) might be motivated by a personal vendetta against Electrum. He said:
“We're not sure what motivates the attacker. It might be some kind of retaliation after we took steps last month in order to prevent phishing attacks. This counter-attack has been effective against phishing because it does not require a lot of legit servers. If you randomly connect to 10 servers, the chance that at least one of them is performing the counter-attack is very high.”
How to protect your Electrum funds
The company said on Twitter that users most at risk are those who downloaded the Electrum software a long time ago and hadn't updated since. At present, according to the website, software versions older than 3.3 cannot connect to public servers.

Electrum users should do the following, according to Electrum:
- Upgrade your Electrum software to avoid receiving phishing messages
- Only download software directly from the official website, electrum.org. If you're not sure, check the security certificate by clicking on the lock icon next to the URL address. (More advanced users can also access their GitHub repositories.)
- Disable the auto-connect option and select your server manually (a short-term solution according to Electrum, until the issue is fixed)
Who's behind the Electrum DoS Attacks?
DoS attacks are often carried out on big web-based servers such as online banking and payment gateways and can be driven by motives such as revenge, blackmail or activism.
In this case, it is rumored to be retaliation by the unknown hackers responsible for December's breach, where a sophisticated trojan virus nicknamed "Electrum Stealer" was eventually thwarted by Electrum, but only after cryptocurrency worth millions of dollars were stolen.
Are Desktop and Mobile Bitcoin Wallets Safe?
Any cryptocurrency wallet can be vulnerable under certain conditions, depending on the precautions the user takes.

Even sophisticated hardware wallets like Ledger and Trezor can be penetrated under controlled conditions by a supply-chain or side-channel attacks, or something as simple as a "$5 wrench attack", where your private keys are extracted by a third party through violent means.
However, computer and phone-only wallets can make for especially easy targets. Here's why:
- They need the Internet: They're "hot" wallets, meaning they need to connect to the Internet and the client-server in order to function and sync with their related blockchain.
- They're Software-based: These wallets are unable to employ the highest safety measures such as a dedicated secure element, encrypted communication, etc. If someone gains access to your computer or phone, for example a co-worker who spied your login PIN, they might be able to crack the device and steal your private keys.
- Volunteers & Freeware: Also, desktop, mobile and web wallets are often created and maintained for free by a community of volunteers who might not always be trustworthy.
- Saved on device: Inexperienced users mostly download their private data to their computers, worried they might lose them. This means that your private information is only as secure as your computer or mobile phone.
If you want to know more about desktop and mobile wallet security issues, read this CoinSutra article.
Is a hardware wallet safer than desktop and mobile wallets?
Without a doubt. The CoolWallet S and other hardware wallets such as Ledger and Trezor offer additional security lines of defense that the attacker has to breach.

In the CoolWallet's case, the hardware wallet is never "hot", in the sense that it only connects to your phone by Bluetooth, not by Internet. The CC EAL5+ secure element and encrypted Bluetooth ensures that the user's private keys are never revealed, not even to the users themselves. While balances are updated on the app, any sending or trading of cryptocurrencies require the transaction to be signed by the Secure Element, which also checks the authenticity of its app through a complicated process which we'll explain in another post.

Lastly, any pending transaction will be displayed on the CoolWallet's e-paper screen and needs to be confirmed with a physical button push.
Therefore, the only realistic way to steal a hardware wallet user's funds, is for the malicious party somehow be in physical possession of both the hardware wallet and the mobile phone (for the app). The hacker likely also needs to know the user's PIN code to unlock the phone and access the app.
Final Thoughts:
This scenario is very unlikely to happen to any crypto owner who values their investment and takes the necessary security precautions to safeguard their virtual currencies.
Ultimately, how you store and protect your cryptocurrency investment is a personal matter.
A Bluetooth hardware wallet like the CoolWallet S, the first Bluetooth mobile hardware wallet (currently retailing at only $99) or the upcoming Ledger Nano X (RRP $129) is an extremely safe option for any serious-minded investor.
However, if you keep your small portfolio on an exchange or a free desktop, mobile or web wallet application, please DYOR (do your own research) and make sure you select a good project with an active community that frequently issues newly updated firmware.
Just remember though:
That fraction of a Bitcoin you're storing on your phone or computer right now, might be worth a fortune one day. So treat it as such.
By Werner Vermaak
Disclaimer: CoolBitX does not endorse and is not responsible for or liable for any content, accuracy, quality or other materials on this page. Readers should do their own research before taking any actions.
CoolBitX is not responsible, directly or indirectly, for any damage or loss caused by or in connection with the use of or reliance on any content, goods or services mentioned in this guide.






Share:
J’Accuse…! Ledger Vs Trezor – Who’s Right?
ATTENTION: CoolWallet BNB Holders, Move your BNB to Binance for Mainnet Conversion